Edge Architecture
Overall Architecture
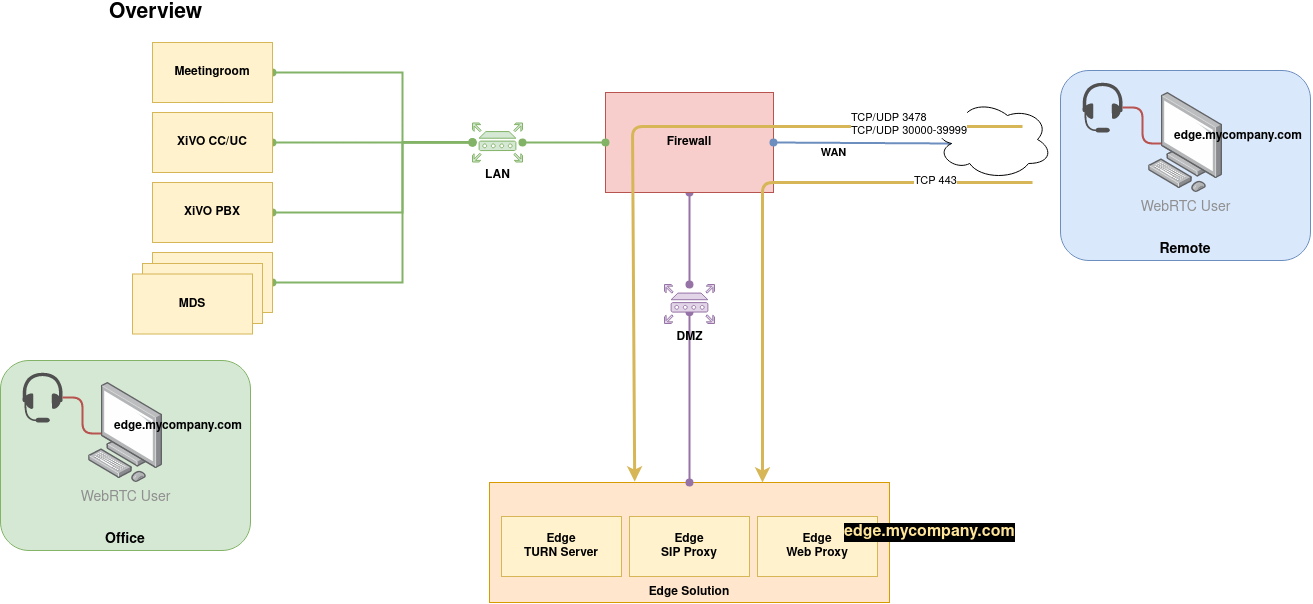
As you can see on the schema above the Edge Solution is to be put inside one’s company DMZ.
From the external world only the Edge Solution will be seen. Only HTTPS and TURN flows should be authorized from the external - see Network Flows for more details.
The Edge Solution is composed of three components:
a Web Proxy
a SIP Proxy
and a TURN Server
These components can be installed:
on 3 separate servers - see 3 Servers Installation
or on 1 server - see 1 Server Installation
Network Flows
From the outside (WAN to DMZ)
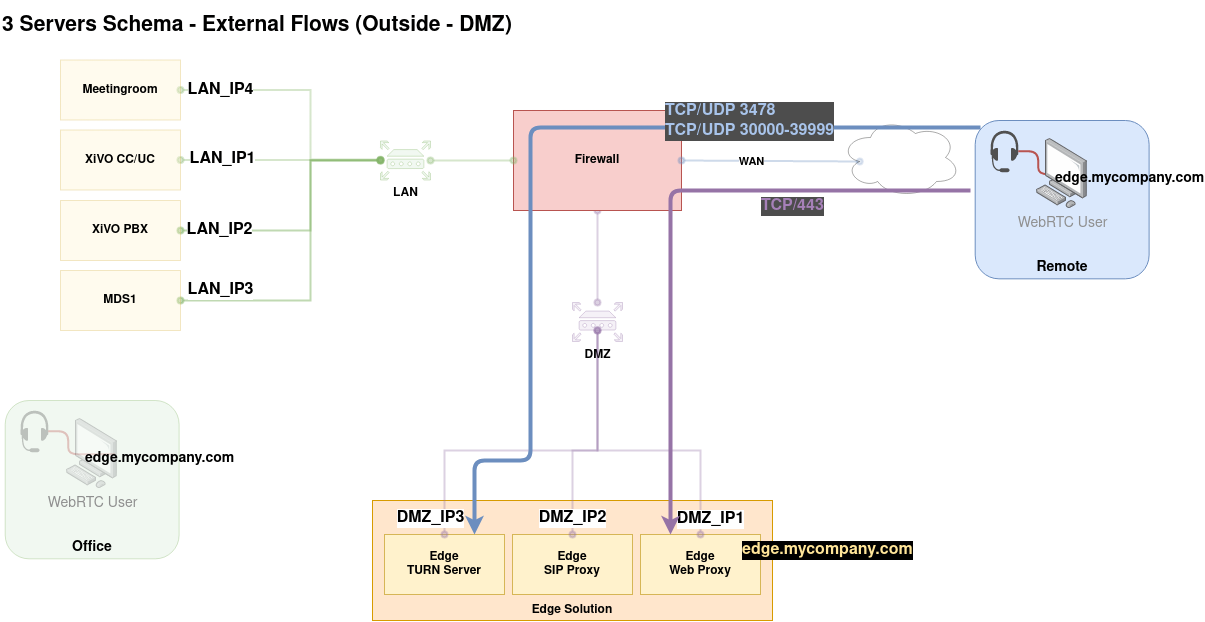
From |
To |
Ports to open |
Usage |
|---|---|---|---|
Outside
|
Web Proxy
|
|
UC Application from External Users |
Outside
|
TURN Server
|
|
STUN/TURN via UDP, TCP |
Outside
|
TURN Server
|
|
RTP Flow between remote WebRTC client and TURN Server |
Internally (DMZ to LAN)
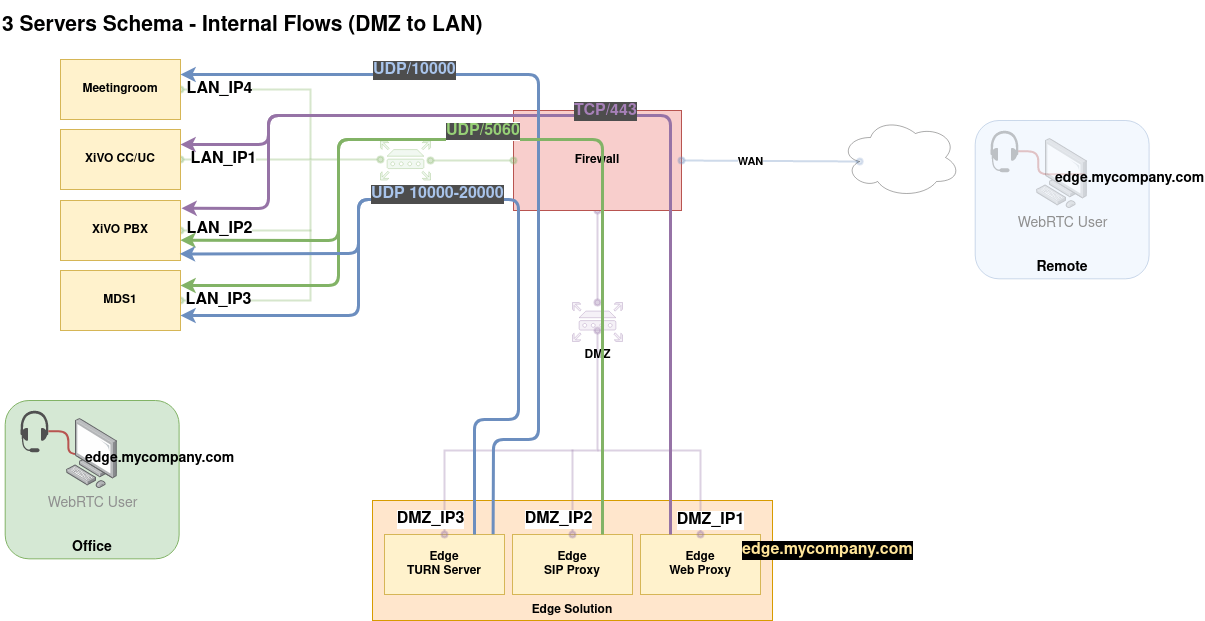
From |
To |
Ports destination |
Usage |
|---|---|---|---|
Web Proxy
|
XiVO CC
|
|
Proxified UC application from Edge towards CC/UC Server |
TURN Server
|
Mediaservers (inc. Main)
|
|
RTP flow between TURN Server and Asterisk(s) |
SIP Proxy
|
Mediaservers (inc. main)
|
|
SIP flow between Asterisk(s) and SIP Proxy |
Supplementary ports for Meetingroom (DMZ to LAN)
If you have a Meetingroom server in your installation you must also open these ports from the DMZ towards the LAN:
From |
To |
Ports to open |
Usage |
|---|---|---|---|
Web Proxy
|
XiVO
|
|
Proxified Meetingroom API from Edge towards XiVO Server |
TURN Server
|
Meetingroom
|
|
RTP flow between TURN Server and Meetingroom (when using TURN) |
Internally (LAN to DMZ)
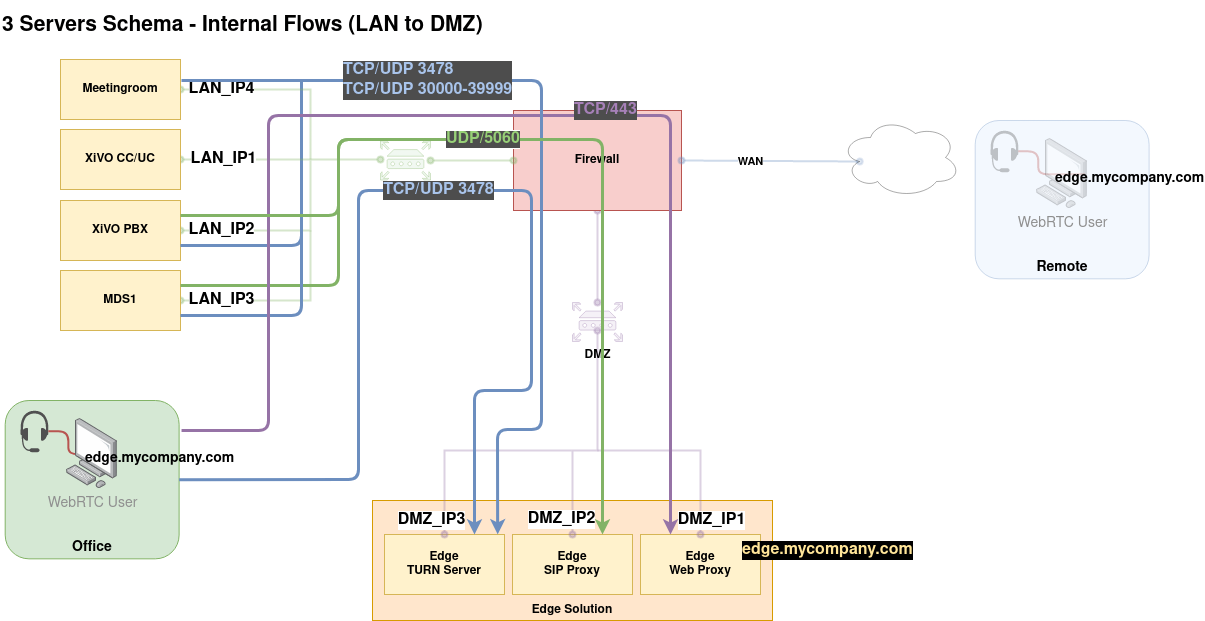
Here are the flow to open between the LAN towards the Edge servers (LAN to DMZ):
From |
To |
Ports to open |
Usage |
|---|---|---|---|
UC Clients
|
Web Proxy
|
|
UC Application for Internal Users |
UC Clients
|
TURN Server
|
|
STUN/TURN requests between UC Clients and TURN Server |
Mediaservers (inc. Main)
|
SIP Proxy
|
|
SIP flow between Asterisk(s) and SIP Proxy |
Mediaservers (inc. Main)
|
TURN Server
|
|
STUN/TURN requests between Mediaservers and TURN Server |
Mediaservers (inc. Main)
|
TURN Server
|
|
RTP flow between Asterisk(s) and TURN Server |
Supplementary ports for Meetingroom (LAN to DMZ)
If you have a Meetingroom server in your installation you must also open these ports from the LAN towards the DMZ:
From |
To |
Ports to open |
Usage |
|---|---|---|---|
Meetingroom
|
TURN Server
|
|
STUN/TURN requests between Meetingroom and TURN Server |
Meetingroom
|
TURN Server
|
|
RTP flow between Meetingroom and TURN Server |
Inside DMZ
From/To |
To/From |
Ports to open |
Usage |
|---|---|---|---|
Web Proxy
|
SIP Proxy
|
|
Websocket for SIP |
This is probably unneeded (traffic between servers inside the DMZ should be in most of the cases unfiltered), but if it would be the case this flow must be authorized.